The CertiK-Kraken Controversy: Exploring a Complex Case of Blockchain Security and Ethical Hacking

The cryptocurrency exchange Kraken recently found itself at the center of a controversial security breach involving CertiK, a blockchain security company. This incident, which began as a routine white-hat hacking exercise to identify potential vulnerabilities, escalated into allegations of extortion and legal threats, raising significant questions about the ethics of security testing and vulnerability disclosure in the blockchain industry.

Background of the Incident
The situation unfolded when CertiK, during a security testing exercise, identified critical vulnerabilities in Kraken’s systems that could allow artificial balances to be created on user accounts. CertiK claimed that during their tests, which were intended to simulate attacks and identify vulnerabilities, they were able to manipulate account balances by exploiting flaws in Kraken’s deposit system. The exercise revealed that millions of dollars could be erroneously credited to any Kraken account, highlighting a severe security oversight.
The Allegations and Responses
Kraken responded to the breach by describing the incident as extortion, claiming nearly $3 million was siphoned off due to the exploited vulnerabilities. CertiK, on the other hand, defended their actions as part of a responsible security test, meant to benefit Kraken by identifying and helping to rectify critical security flaws. They argued that their intention was never to harm or steal from Kraken but to improve the platform’s security infrastructure.
CertiK also mentioned that they were given too little time to return the funds and were not provided with appropriate directions or a specific wallet address for returning the funds, complicating the resolution of the incident. The situation was further exacerbated when Kraken allegedly threatened CertiK employees, demanding the immediate return of the funds, which CertiK claimed added unnecessary tension and delayed resolution.
Legal and Ethical Implications
This incident has sparked a broader discussion within the cryptocurrency community about the boundaries of ethical hacking and the protocols for disclosing security vulnerabilities. Legal experts and community members have debated whether CertiK’s actions crossed the line from ethical vulnerability testing into extortion, given the request for a payment based on the potential damage of the exploit.
Furthermore, the use of a sanctioned tool like Tornado.cash by CertiK to allegedly obfuscate the transaction records has brought additional scrutiny and potential legal implications, given the sanctions status of such tools in the United States.
Community and Industry Impact
The repercussions of this incident are far-reaching, affecting not just CertiK and Kraken but also the broader perception of security within the blockchain industry. It underscores the need for clear guidelines and standards for ethical hacking and vulnerability disclosure, particularly in industries as sensitive as cryptocurrency, where security is paramount.
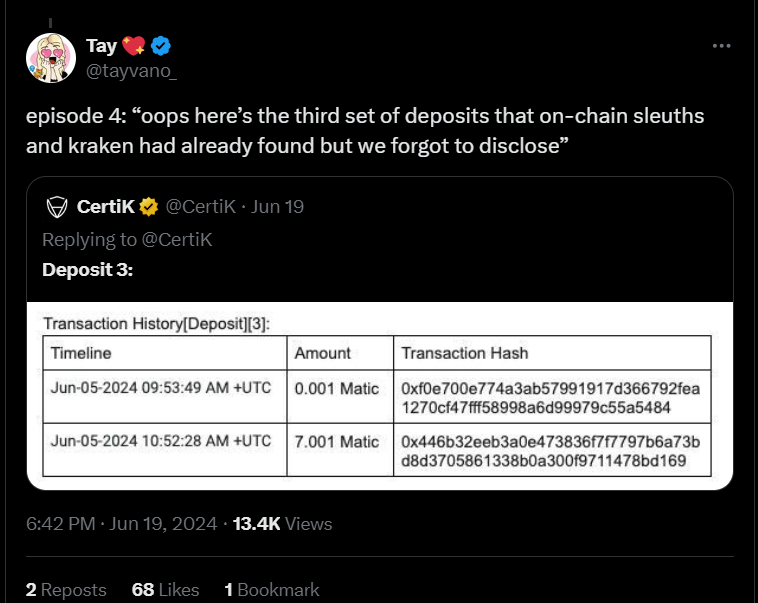
The community response has been mixed, with some defending CertiK’s approach as a necessary part of strengthening crypto exchanges against real-world threats, while others criticize the method and transparency of the testing and disclosure process. Taylor Monahan, a respected figure in the Ethereum community, raised concerns about potential damage to CertiK’s reputation and internal culture. Her commentary highlighted the gravity of the situation, given CertiK’s history with previous audits that led to exploits, sparking speculation about possible insider activities. See Tay’s comment
Conclusion
As the dust settles, this incident between Kraken and CertiK serves as a crucial case study for the crypto industry, highlighting the delicate balance between aggressive security testing and ethical conduct. It also emphasizes the need for robust communication channels and predefined protocols to handle such vulnerabilities responsibly, ensuring that both security firms and crypto exchanges can work together to fortify the ecosystem against genuine threats.
