Yearn Finance Loses $11.5 Million in Security Breach Due to Misconfigured yUSDT Minting

Overview:
On April 13, 2023, Yearn Finance suffered a loss of approximately $11.5 million due to a security breach that allowed an attacker to mint additional yUSDT tokens. This was possible due to a misconfigured iUSDC address during deployment, which allowed the attacker to generate additional tokens using a small deposit of USDT.
The attacker took advantage of the misconfiguration of the yUSDT token on Yearn Finance and used Fulcrum’s iUSDC token instead of the intended iUSDT token. This allowed the hacker to mint 1.2 quadrillion yUSDT tokens with a $10,000 deposit, which were then exchanged for various stablecoins such as DAI, USDC, BUSD, TUSD and USDT.
Although it used Aave V1 for a series of swaps, the Aave team confirmed that its protocol was not exploited in the attack and that Aave V1 was not affected and stressed that the root cause of the hack was the misconfigured yUSDT token, not Aave.
About the attacker :
-
Address : 0x5baC20BEef31d0ECCb369A33514831eD8e9cdfE0
-
Wallet 1: 0x16Af29b7eFbf019ef30aae9023A5140c012374A5
-
Wallet 2: 0x6f4A6262d06272c8B2E00Ce75e76d84b9D6F6aB8
Aave Lending pool V1 Contract:
-
Address: 0x398eC7346DcD622eDc5ae82352F02bE94C62d119
Vulnerable yUSDT contract:
-
Address: 0x83f798e925BcD4017Eb265844FDDAbb448f1707D
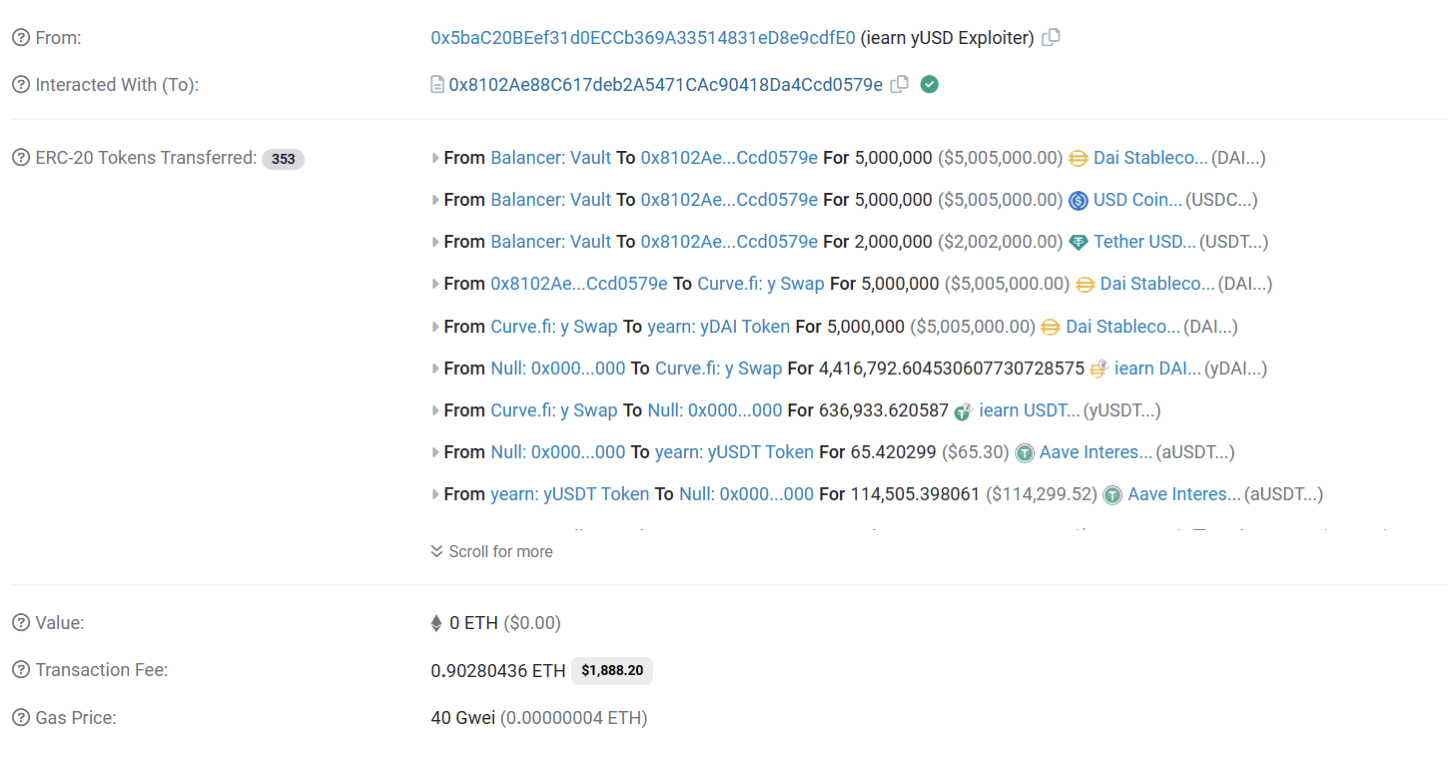
Overview of the transaction :
-
Transaction Hash: 0xd55e43c1602b28d4fd4667ee445d570c8f298f5401cf04e62ec329759ecda95d
Let’s break down the attack :
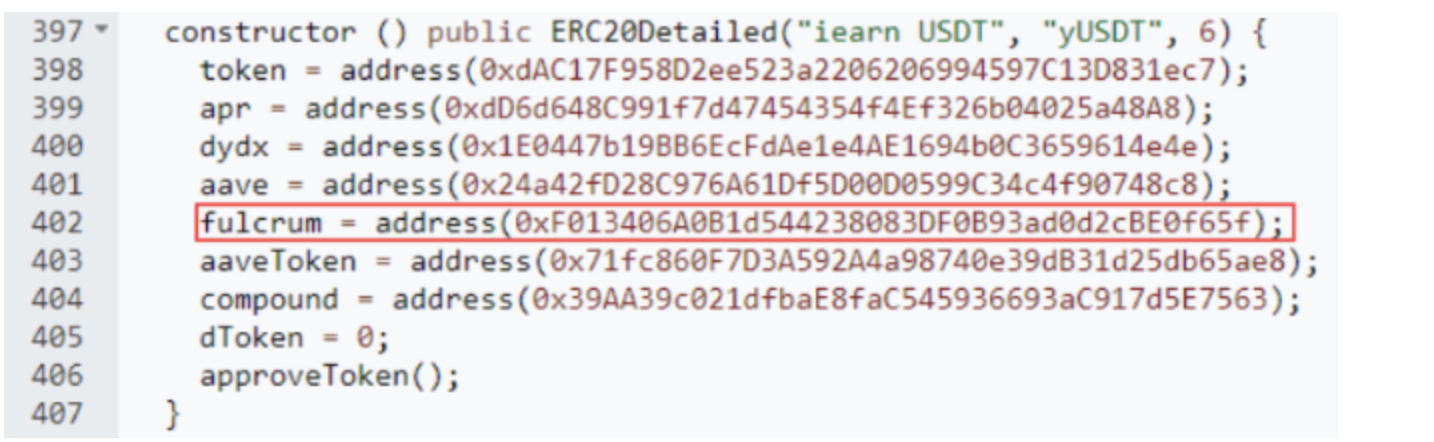
The root cause of the attack on Yearn Finance was a misconfiguration that caused the rebalancing of pools to rely on an incorrect underlying token. One of the strategy pools, Fulcrum, was configured with the wrong address, with USDC being the underlying token of the misconfigured pool.
The attacker initiated the attack by funding it with 10 ETH using TornadoCash on April 11th, 2023, and then created a malicious contract on April 13th, 2023.
The attacker obtained a flash loan to fund the attack and gradually paid back the USDT loan with the Aave pool.
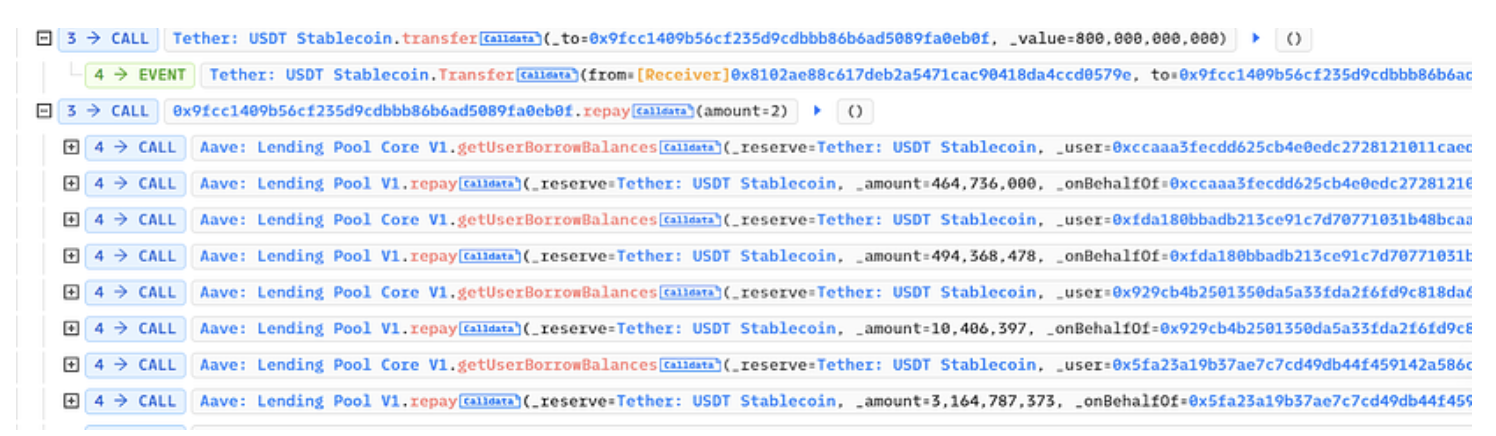
The attacker carried out a sophisticated attack that exploited two DeFi protocols: Aave V1 and yUSDT/ycUSDT. Aave V1 is a decentralized lending platform that allows users to deposit their cryptocurrencies and earn interest on them. The interest rate offered by Aave V1 is algorithmically adjusted based on the supply and demand of the deposited assets. The attacker managed to exploit a vulnerability in the interest rate model of Aave V1, which allowed them to empty the interest rate of the platform, potentially causing a significant loss of funds for depositors.
Additionally, the attacker directly transferred Fulcrum USDC, a stablecoin, to the yUSDT/ycUSDT pool. This pool involves a combination of USDT and cUSDT, and the attacker may have attempted to manipulate the value of the pool by taking advantage of price discrepancies between these assets. By transferring Fulcrum USDC directly to the pool, the attacker triggered a rebalancing mechanism that automatically adjusted the portfolio to maintain the desired ratios of the assets.
In this particular case, the attacker utilized a vulnerability in the bZxUSDC minting process to manipulate the price of yUSDT. bZxUSDC is a token created by the bZx protocol that represents the value of a USDC deposit in the protocol’s lending pool. By minting bZxUSDC tokens, the attacker was able to access the lending pool and manipulate the price of yUSDT, which is another token that represents the value of a USDT deposit in the same pool.
The price of yUSDT had been raised due to a misconfiguration that occurred when the Fulcrum iUSDC token was utilized instead of the intended Fulcrum iUSDT token. This misconfiguration had persisted since the contract’s release, and the address for the Fulcrum had been misconfigured, allowing the attacker to take advantage of the situation.
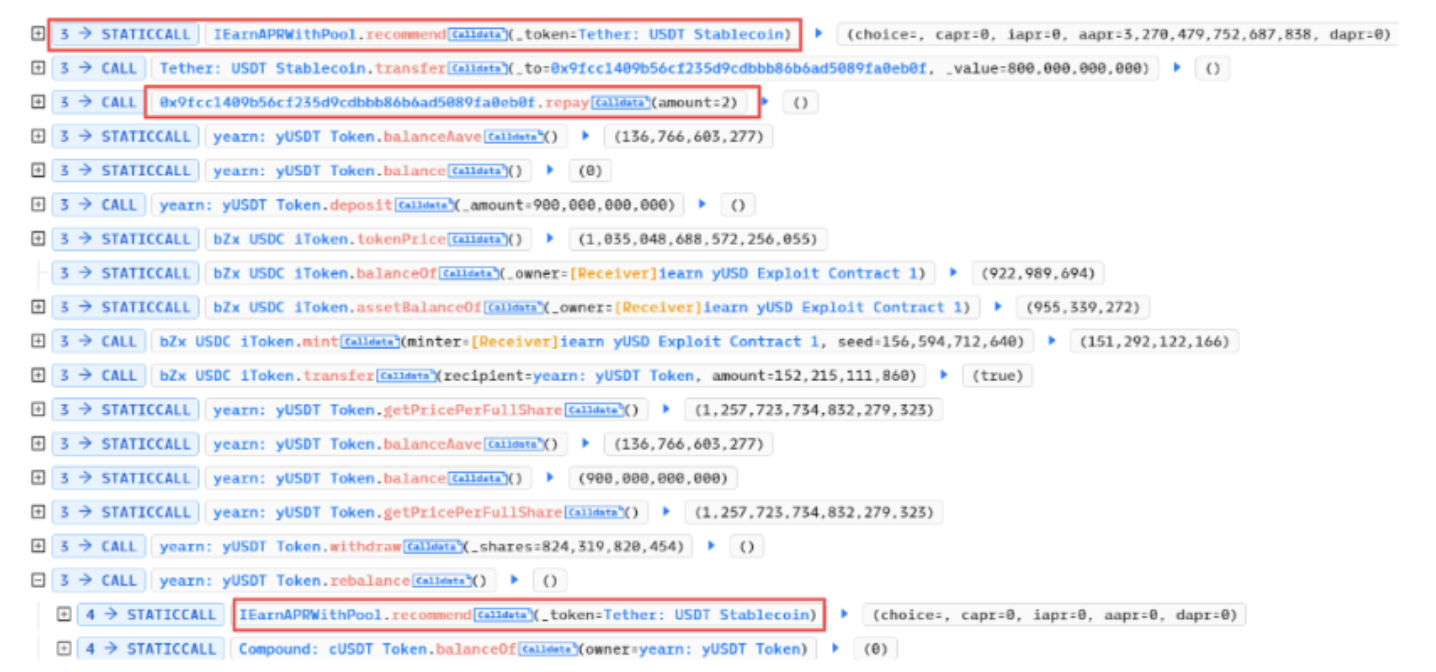
This caused yUSDT/ycUSDT to retrieve a large amount of USDC, mistakenly thinking that its own balance was 0. The attacker then used the Curve Swap function with significantly imbalanced share prices and exchanged the incorrectly calculated yUSDT for stablecoins which added up to a loss of $11.5M and the flashloan was repaid.
Exploit conculsion :
Overall, the attacker’s actions demonstrate the complex and interconnected nature of the DeFi ecosystem, as well as the potential risks and vulnerabilities that exist within it. By exploiting weaknesses in one protocol, the attacker was able to affect the operation of another protocol and potentially cause financial losses for users. and The attacker’s actions were able also to exploit bZxUSDC vulnerability and cause a significant rebalancing of the pool, which could have resulted in financial losses for users.
The incident highlights the importance of thorough testing and auditing of DeFi protocols to prevent such vulnerabilities from being exploited. In this case, a misconfiguration error allowed the attacker to access the pool and manipulate the price, demonstrating the need for careful attention to detail in the development and deployment of smart contracts.
Conclusion:
To maintain the integrity and security of Web3, proactive security measures such as anomaly detection are crucial. By monitoring the blockchain in real time, security platforms can detect anomalies in a timely manner and prevent hacks. Prioritizing proactive security in the still-growing DeFi ecosystem is critical to preventing such exploits in the future and for the Web3 community to build a more resilient and reliable ecosystem that attracts new users and enables a decentralized future.
However, it’s not just about detecting anomalies in real time. It’s also critical to thoroughly test the logic of the code before deploying it to the main network to mitigate potential vulnerabilities and prevent such incidents from occurring. The attack could have been avoided if proper validation and confirmation of the Fulcrum address had been performed during the deployment process before it was hard-coded into the builder and deployed to the production/network environment.
To avoid such vulnerabilities, At SCT ITALIA, we provide smart contract security, examine smart contracts for logical problems and end-to-end security for externally exposed web applications and networks. With the increasing complexity of the blockchain ecosystem, it is vital to engage the services of professional security providers to ensure the safety and integrity of the system.
