A flawed oracle leads to a flash loan attack on the Themis Protocol.

Overview
The ThemisProtocol on Arbitrum was victimized by a flashloan attack, which resulted in the attacker acquiring approximately $370k, and we will discover how the attacker exploited Themis to steal assets.
Introduction to Themis Protocol
The Themis Protocol is a peer-to-peer lending and borrowing platform that operates in a decentralized manner and supports multiple blockchains. As a native crypto trading platform on Layer2, Themis Protocol offers collateralized lending of NFTs, using historical NFT transaction data. Themis is essentially a collection of DeFi protocols, built upon smart contracts. This allows its users to take on varying roles within the governance chain, in accordance with their tolerance for risk, and to earn yields commensurate with their participation.
Vulnerability Assessment
Overview of the Attacker transaction :
-
Transaction Hash: 0xff368294ccb3cd6e7e263526b5c820b22dea2b2fd8617119ba5c3ab8417403d8
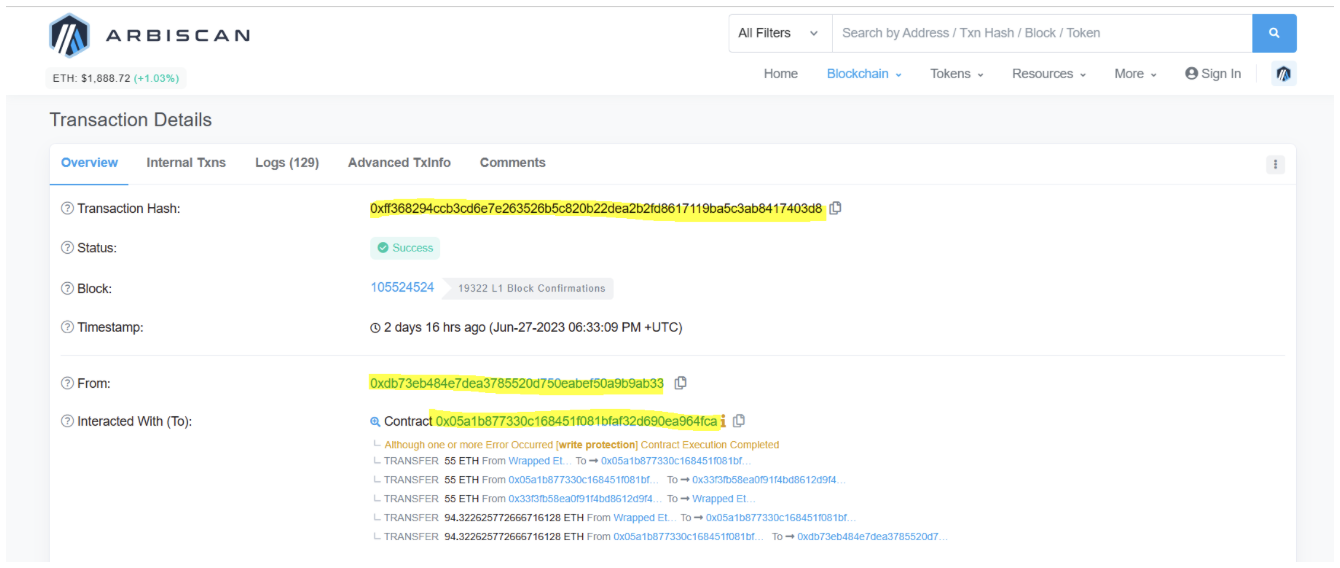
About the Attacker :
-
Address : 0xDb73eb484e7DEa3785520d750EabEF50a9b9Ab33
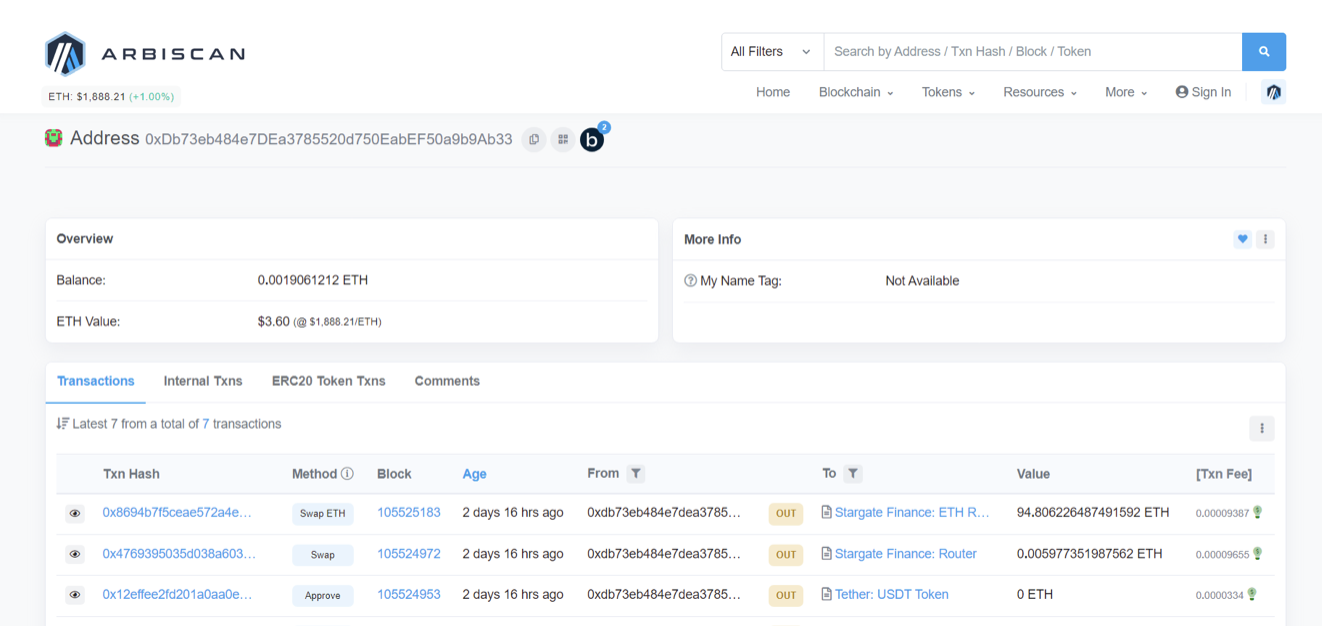
This is the sequence of events that took place:
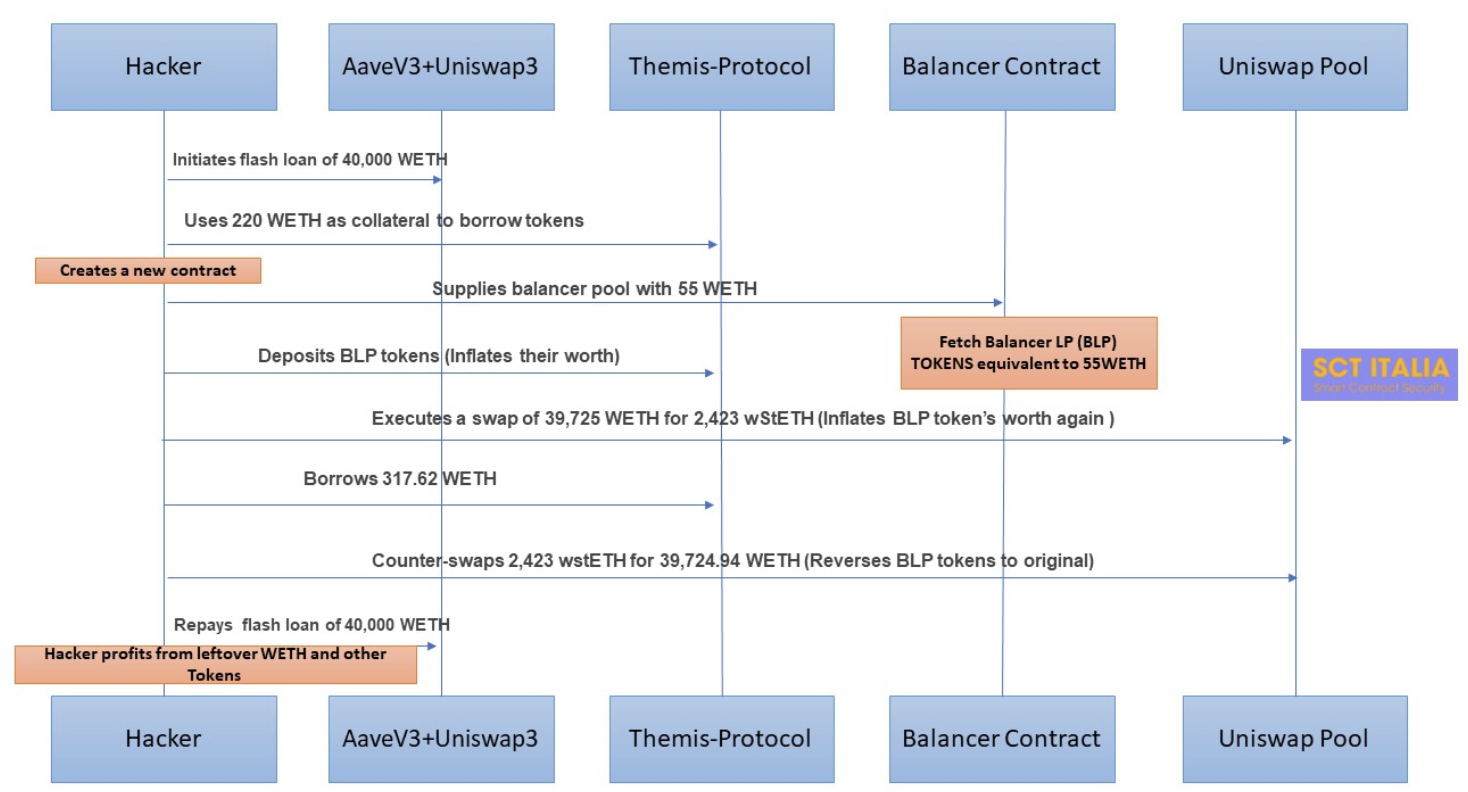
Step1
The hacker initiates a flash loan from Aave v3 and two Uniswap v3 pools to borrow 40,000 WETH without collateral.
Step2
The hacker uses 220 WETH as collateral to borrow DAI, $USDC, USDT, $ARB, and $WBTC from Themis Protocol.
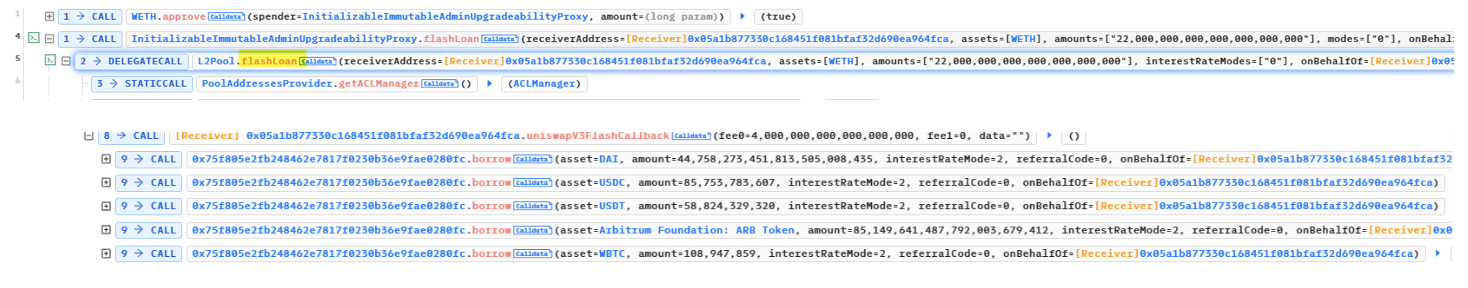
Step3
The hacker then creates a new smart contract and did various operations within it:
Supplies 55 WETH to a balancer pool, fetching 54.665 LP tokens.
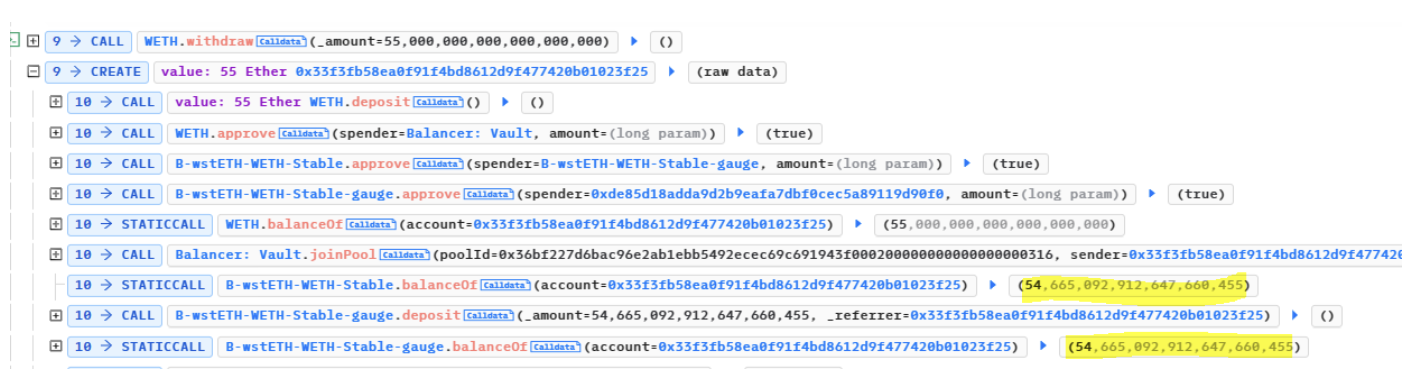
Deposits these BLP tokens into Themis Protocol and manipulates the protocol into believing BLP tokens worth more than their actual value. This is because Themis Protocol relied on a flawed oracle, which provided an inflated price of BLP tokens on the Uniswap price of ETH/USDT.
Executes a swap of 39,725 WETH for 2,423 wstETH, affecting the price of BLP tokens in the balancer pool and further inflating their worth. This swap affected the price of the BLP tokens in the balancer pool, making them appear even more valuable in the eyes of the flawed oracle.
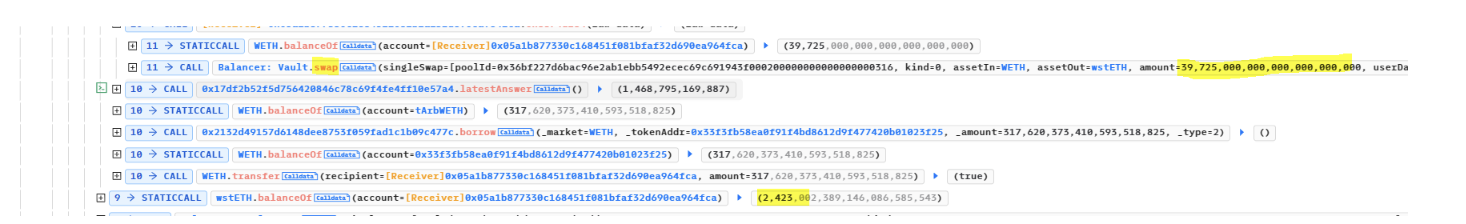
Takes advantage of this manipulated pricing to borrow 317.62 WETH from Themis Protocol.
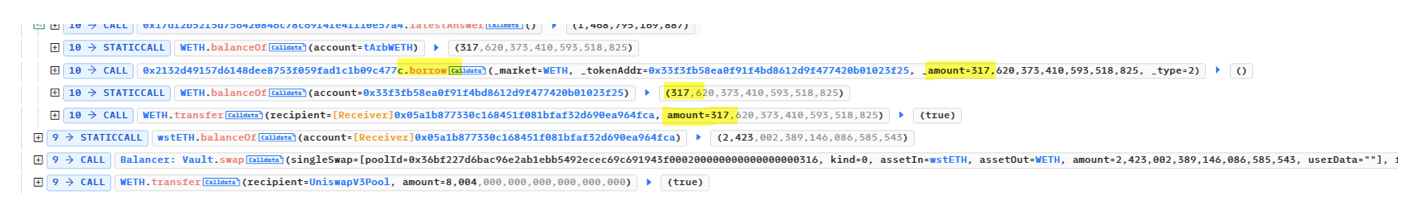
Step4
The hacker then counter-swaps 2,423 wstETH for 39,724.94 WETH, reversing the earlier swapping effect and bringing back the original price value of BLP tokens in the balancer pool.
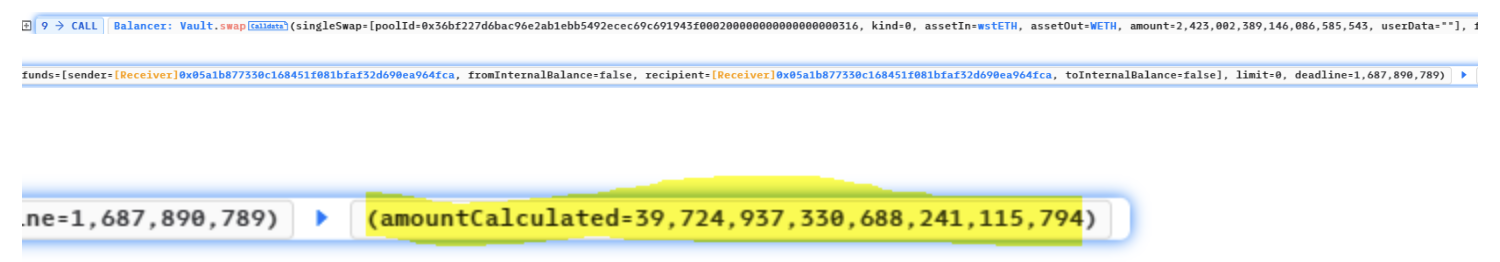
The flash loan from Aave v3 and Uniswap v3 is repaid with 40,000 WETH, and the hacker walks away with his profit made from the leftover WETH and other tokens.
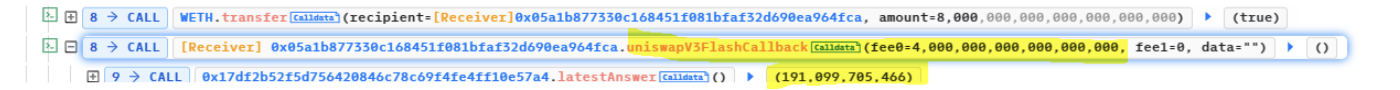
Stolen funds
The stolen funds were cross-chained via Stargate Finance into ETH and remained at this address : https://debank.com/profile/0xDb73eb484e7DEa3785520d750EabEF50a9b9Ab33
The attacker has successfully converted 191 ETH into Tornado Cash, effectively concealing the illicit assets.
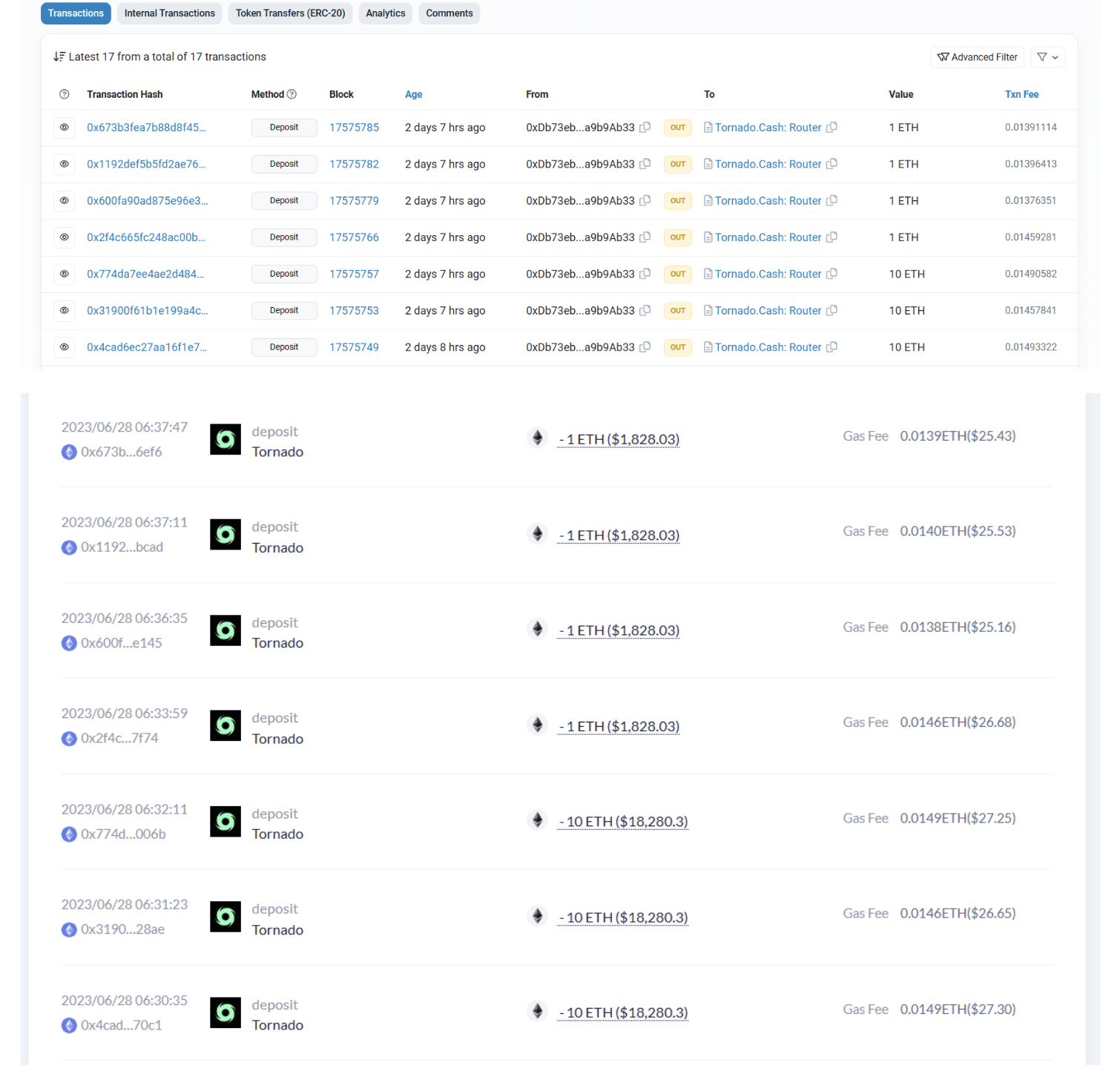
Consequences
In the aftermath of the exploit, the team recognized the incident and announced the temporary suspension of their borrowing functions.
Efforts are underway by the team to recover the funds from the hacker, aiming for a mutually beneficial outcome for all parties involved. In the event of no response or unwillingness from the attacker to cooperate, the team intends to involve authorities to address the problem.
A compensation plan has been established for affected users, and a detailed report on the incident is expected to be shared once the situation stabilizes.
Conclusion
The attack was successful because the attacker manipulated the token price using a flawed oracle. This incident highlights several important principles for ensuring the safety of DeFi projects.
Ensuring the security of the Price Oracle is crucial for DeFi protocols. To mitigate such exploits, it is advisable to use trusted price oracle services that aggregate data from multiple sources and protect against manipulation. Conducting regular contract audits and rigorous testing can help identify potential vulnerabilities and address them before they are exploited.
In addition, developing a well-designed economic model that considers possible attack vectors can reduce the risk of exploitation. This may involve implementing safeguards that limit maximum profits from trades or integrating an automated system that temporarily halts trading in response to significant price changes.
As a network of specialists, SCT ITALIA brings together a team of expert professionals who offer audit security services. Our goal is to assist you in safeguarding your token contract or project, ensuring its security and minimizing the presence of exploitable vulnerabilities. Through our proactive approach to securing your projects, we aim to mitigate the risk of financial losses and provide protection for the investments made by your users.
